|
|

One of our PhD students Lars Lydersen at work. | |
| | 
Our lab logotype, representing here a “faked state” that Eve sends to Bob in this attack. |
We used the same attack to crack systems from two vendors; here is one of them.
Below you can see the secure communicating boxes with their internals exposed, Alice at left and Bob at right.
In a typical installation they get separated by tens of kilometers of fiber.
Our main interest in this attack was to gain control of the single-photon detector in Bob; the next picture shows a close-up of its electronics board.
This detector board was quite complicated at the first look. We had it X-rayed in an attempt to see internal layers in the board, not visible by other means.
Although with a proper contrast adjustment some of the internal copper could be seen (check larger image),
there was too much visual noise to track the traces. Looking at the X-ray was fun but completely useless.
Lars ended up brute-forcing the connections with an ohmmeter, reverse-engineering just enough of the circuit
to understand that it should allow the attack. |  |
Here are the instruments we used to test the system and confirm the vulnerability.

A signal generator to run the laser. This unit (P400 from Highand Technology) is quite versatile and costs some 4 k€; we use it in many lab experiments.
Actually, cheaper signal generators that can synchronize to a 0.6–5 MHz external trigger would do
in this experiment. | 
A variable optical attenuator, to precisely set the laser power applied to Bob during tests.
A similar computer-controlled unit without a display currently costs
less than 1 k€. | | | 
A fiber-pigtailed laser diode to produce light pulses (a small yellow package at the bottom; the rest is a heatsink and a temperature controller).
For this particular test almost any telecom laser would do, at a few hundred euro. This chip cost us almost 2 k€,
due to its top-notch specs. | 
A power meter, to check laser power. Costs a few hundred euro. |
In addition to these, we needed an oscilloscope (1 GHz bandwidth, with an optical probe) and some voltmeters.
Here you can see Lars using them all on the running quantum key distribution system.
The blue monitors belong to Alice and Bob, and display internal diagnostics at the two sides of the secure link.
In these experiments we have confirmed that the vulnerability has all the “right” characteristics which make it fully exploitable.
Building a complete eavesdropper looks very doable (we propose a scheme in the paper), but one would need an extra set of quantum key distribution boxes
(which retail at around 100 k€ a set) to make this eavesdropper.
Last year we have implemented a full eavesdropper on another, non-commercial cryptosystem,
but I digress. Back to our muttons lads and girls, here is the other commercial system we cracked:
 |
Commercial systems similar to the one we have tested are used to encrypt network traffic. Here is one such network node in Switzerland.
The two black quantum boxes at the bottom generate secret keys with two other nodes kilometers away.
The rest of the rack is classical cryptographic hardware using these keys. |
You may have some deja vu, as the inside of this commercial system looks pretty similar. Here are the boxes opened, and the detector board.
By the way these rack cases are mildly tamper-proof: if you want to open them without steel-cutting tools, you need to get a key from the manufacturer.
If you are really interested in the content of these boxes, read a good free paper that describes it.
The detector electronics in this system was cleanly designed. We had no problem identifying all the active components and reverse-engineering the entire circuit diagram.
(ID Quantique asked us to keep the resolution of this picture low, to protect their commercial information.)
The security loophole we have exposed is intrinsic to a whole class of single-photon detectors, regardless of their manufacturer and model.
However we had to reverse-engineer each system, to see what we are doing and also to illustrate
the principle.
|  |
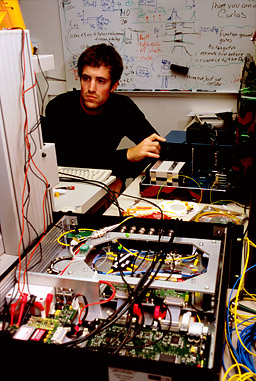 |
Here is Lars again, testing Bob’s box.
On the foreground you can see many electrical connections made to the detector board, to monitor signals at different points.
This allowed us to neatly illustrate in the paper what happens in the circuit during the attack.
Hacking IDQ’s system was done in collaboration with the Max Planck institute for the science of light and
the University of Erlangen-Nürnberg.
Additional eavesdropping methods were discovered during this work:
♦ C. Wiechers et al., “After-gate attack on a quantum cryptosystem,” arXiv:1009.2683 [quant-ph].
♦ L. Lydersen et al., “Thermal blinding of gated detectors in quantum cryptography,” arXiv:1009.2663 [quant-ph].
|
This security vulnerability was responsibly disclosed to both system manufacturers, several months prior to its public release.
(Hey, we did responsibly disclose the problem: here is a bunch of IDQ engineers feeding us pizza
in their Geneva office and discussing how to patch it :).
Watch news on NRK1 (2 min video).
Selected press coverage in English:
Nature News |
Slashdot |
International Business Times |
TechRepublic |
Ars Technica |
PopSci |
Bruce Schneier |
PC Pro |
Techworld |
The Register |
eWeek |
ZDNet |
GCN |
InformationWeek |
in German:
Frankfurter Allgemeine Zeitung (PDF) |
in French:
Le Figaro |
market.ch |
in Norwegian:
audio interview with Lars Lydersen on NRK Verdt å vite (MP3, 14 min) |
more on studentradioen (MP3, 5 min) |
forskning.no (also in Danish) |
digi.no |
NRK Trøndelag |
Teknisk Ukeblad |
Gemini |
Elektronikknett |
Adresseavisen |
Universitetsavisa |
in Russian:
Компьюлента |
in Chinese:
新华网.
Page authored by Vadim Makarov who worked in every experiment but was unfortunately behind the camera during all photo ops.
| |  |
|










